What is Cryptolocker:
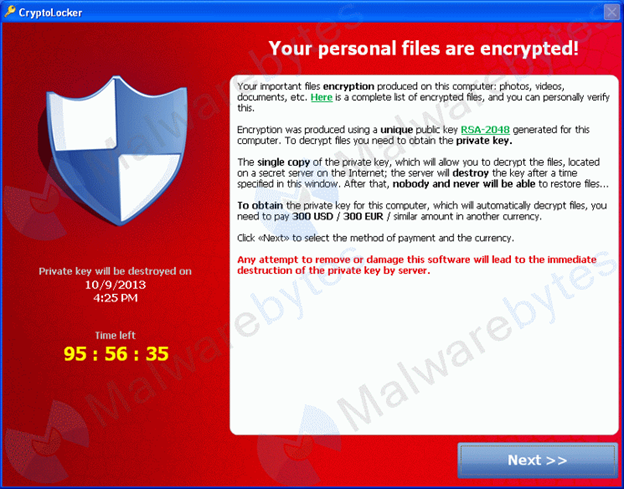
CryptoLocker is a ransomware program that was released around the beginning of September 2013. This ransomware will encrypt certain files using a mixture of RSA & AES encryption. When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either $100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days, to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files. This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
Method of Infection:
As of this time, the primary means of infection appears to be phishing emails containing malicious attachments typically disguised as a PDF file attachment or other type of document. The victim must launch the file on the computer for this to infect the computer. The infection will then attempt to find a live Command & Control server, it will communicate with it and receive a public encryption key that will be used to encrypt your data files. It will then store this key along with other information in values under the registry key under HKEY_CURRENT_USER\Software\CryptoLocker. Unfortunately, the private key that is used to decrypt the infected files is not saved on the computer but rather the Command & Control server.
CryptoLocker will then begin to scan all physical or mapped network drives on your computer for files with the following extensions: *.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, *.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c. When it finds a files that matches one of these types, it will encrypt the file using the public encryption key and add the full path to the file and the filename as a value under the HKEY_CURRENT_USER\Software\CryptoLocker\Files Registry key.
When it has finished encrypting your data files it will then show the CryptoLocker screen as shown above and demand a ransom of either $100 or $300 dollars in order to decrypt your files. This ransom must be paid using Bitcoin or MoneyPak vouchers. It also states that you must pay this ransom within 96 hours or the private encryption key will be destroyed on the developer’s servers. Paying this ransom does not necessarily mean that the de-encryption will happen however.
How do we prevent this virus?
US-CERT recommends users and administrators take the following preventative measures to protect their computer networks from a CryptoLocker infection:
- Do not follow unsolicited web links in email messages or submit any information to webpages in links
- Use caution when opening email attachments.
- Maintain up-to-date anti-virus software.
- Perform regular backups of all systems to limit the impact of data and/or system loss – local workstations should have system restore enabled.
- Secure open-share drives by only allowing connections from authorized users.
- Keep your operating system and software up-to-date with the latest patches.
What will happen if I get infected?
If a machine becomes infected immediately disconnect the infected system from the wireless or wired network. This may prevent the malware from further encrypting any more files on the network.
Depending on the situation, files may be recovered on the local computer via system restore, provided that this virus has not mutated to include those files as well. Then, after recovery attempts are completed one should format and reinstall the computer to erase any potential hidden reinfection attempts.
Update: According to Bleeping Computer, Cryptolocker now has mutated so that it will also delete the Windows Volume Shadow Copy file store rendering the computers ability to recover data via this method moot. Now the only way seemingly would be to recover from cold or offline backup.
Further information can be found here: http://www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
Other sources: http://www.us-cert.gov/ncas/alerts/TA13-309A

